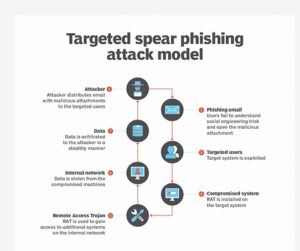
This post will explain Ways to prepare for a phishing attack. Phishing is a kind of cybercrime that includes the deceitful practice of sending e-mails from reputable companies to cause people to expose individual information, such as passwords and credit card information.
Best 5 Ways To Prepare For a Phishing Attack
In this article, you can know about Ways to prepare for a phishing attack here are the details below;
Phishing has actually been around for a very long time, however it’s getting more sophisticated every day, with new techniques being discovered by hackers who are always looking for new ways to deceive you. In this blog post, you’ll find out about “10 things” you can do when phisher targets you; your defenses are ready and ready.
What Is a Phishing Attack?
Phishing attacks are hackers’ efforts to take your individual information, such as passwords and credit card numbers. These hackers will generally send you e-mails or pop-up ads with links that result in phony sites created to look like the real ones so they can take your login qualifications. Also check what is a bug
Phishing is a rip-off where hackers send out emails or texts pretending to be from a reliable business and ask for your individual information, such as your Social Security Number. These scams are also called “business e-mail fraud.”
Ways to Secure and Prepare Yourself for Phishing Attacks
Phishing rip-offs are frequently made more believable by including popular brand names, logos, mottos, and colors of these business in their website style. Once a person comes down with a phishing site, they might be asked to enter their e-mail accounts’ charge card numbers or login credentials.
For a phishing attack to be effective, it needs only 3 things:
– a target (you),.
– a pretext (a reason), and.
– a delivery approach (an e-mail).
It’s vital for everyone who uses any kind of internet-connected device– smartphones, tablets, or computers– to understand how this phishing works so that they can avoid ending up being a victim.
Here are “10 ways” you can prepare and safeguard yourself against phishing attacks:.
1) Be careful of unforeseen emails.
Phishers will attempt to persuade you to visit their website by sending out an email disguised as being sent from a reliable source. These emails might appear genuine, consisting of logo designs and colors of popular brand names.
However if you get an e-mail requesting your login credentials for any reason, do not click the link. Be suspicious of emails from unidentified e-mail addresses or with odd attachments.
2) Inspect the sender address.
Take a look at the sender’s email address to see if it’s coming from where it states. Many phishing frauds will appear to come from a trusted website (e.g., eBay), however the sender’s address will be something like PayPal , which is not eBay’s actual e-mail address.
Numerous phishing scams utilize an address similar to among the genuine addresses of the individual or business they try to impersonate. For-example, if you get an email from” [email protected]” and you know that PayPal’s domain name is” paypal.com, “this ought to be a red flag right away.
If it states something like” hacked_emailaddress @ website_of_attacker,” nevertheless, there isn’t as much cause for concern– unless you take place to be using the exact same password all over, in which case someone may currently have access to your other sites as well.
It’s also possible for somebody with bad intentions to spoof the address of someone else who has nothing to do with the email– this practice is called “email spoofing.”.
3) Hover over any links.
Hover your mouse pointer over any web links consisted of in the emails and take a look at their addresses in the bottom left corner of your internet browser (without clicking them). Phishing rip-offs usually connect to non-legitimate sites that will collect your individual details for identity theft purposes or just utilize a fake site that looks genuine. For this reason, you believe you are logging into the actual website (e.g., PayPal), but in reality, you are not.
4) Check the brief links consisted of in the e-mail.
If a string of letters and numbers follows any of the links included in the email, these confidential “reduced” links might be used to track your web usage or perhaps put malware on your computer.
These links reroute to legitimate sites, however they can also be used for phishing considering that it is harder to see something after the reduced link (i.e., it looks like it goes directly to an eBay login page). It is advised to type out the URLs yourself to sites you trust instead of clicking on brief links.
5) Examine the e-mail headers.
In some cases, users or security business can check the header info for a suspicious email and find out where it came from. This is not constantly possible, however, as the header details can be spoofed or changed.
6) Use a spam or junk e-mail filter.
Many e-mail provider provide spam and junk mail filters, which will help you recognize and get rid of potentially harmful messages prior to they reach your inbox. Spam and junk filters can be extremely efficient versus phishing frauds, especially since these e-mails typically contain several crucial characteristics that blatantly promote them as phishing efforts.
However, even the best filtering programs typically miss out on some prospective hazards, so it is important to stay alert when using such programs. Additionally, expect the phisher can navigate your spam filter (and many of them do). Because case, they may get to your account and possibly cause damage or set up harmful software in addition to sending more phishing e-mails with impunity. Many people appear to use spam filters with some degree of success. Also check Wireshark alternatives
7) Check for grammar, spelling, and format mistakes.
Lots of spammers do not pay much attention to their messages’ details, resulting in bad grammar, misspellings, or inaccurate format. Attackers who have a greater level of ability might be able to avoid being so quickly identified. However, these kinds of errors can still assist you to determine a potentially deceptive e-mail.
8) Treat any hyperlinks suspiciously.
In many phishing frauds, links consisted of in e-mails do not contain specific directions regarding what must be done after clicking them. In other cases, the text consisted of with the link may recommend something, while an image on the very same page recommends something else altogether. In either case, it’s best not to click on these links unless you know for sure where they will take you.
9) Expect generic salutations and greetings.
Lots of phishing e-mails are not customized, which ought to be another warning sign that something may not be right. If you receive an e-mail from your bank that begins with a generic welcoming like, “Dear valued consumer,” you may wish to examine even more prior to opening any attachments or clicking any links. This method might conserve you some distress down the road.
10) Check SSL Certificate.
Make sure that any website where you offer individual info has an SSL certificate installed. If you send out delicate information over a non-secure connection, no matter how safe the website appears, all of your material could be obstructed by unapproved celebrations. Moreover, if there isn’t an SSL certificate installed on any site that deals with. Also check Unzip password protected zip file Windows 10
Final Ideas.
In a significantly phishing-prone world, it’s necessary to take the needed precautions. We have a couple of pointers to assist you prepare for a potential attack and avoid being scammed out of your identity or personal information. What are some other ways people can secure themselves from phishing rip-offs?